
High profile cyber attacks have been increasing in recent years and the methods used by cyber criminals are constantly evolving. In 2019, the New York Senate passed a security law designed to protect personal information from cyber attacks by placing requirements on businesses. This law is called The Stop Hacks and Improve Electronic Data Security Act (SHIELD).
It's important to note that your business does not need any physical presence in New York for the Act to apply to it. SHIELD applies to any medium or large company that holds the computerized personal data of citizens of New York. Small businesses do not have to comply with SHIELD.
The act aims for businesses to improve their cyber security defenses by requiring them to implement 'data security programs.'
In addition, companies must implement 'reasonable security safeguards' to keep personal data safe from cyber criminals. These safeguards help to keep data secure and confidential. They also ensure data is safely stored and erased in a timely manner.
Our Free Privacy Policy Generator helps you create a custom Privacy Policy for your website and mobile app. Just follow these few simple steps and your Privacy Policy will be ready to display in minutes.
- Click on the "Free Privacy Policy Generator" button, located at the top of the website.
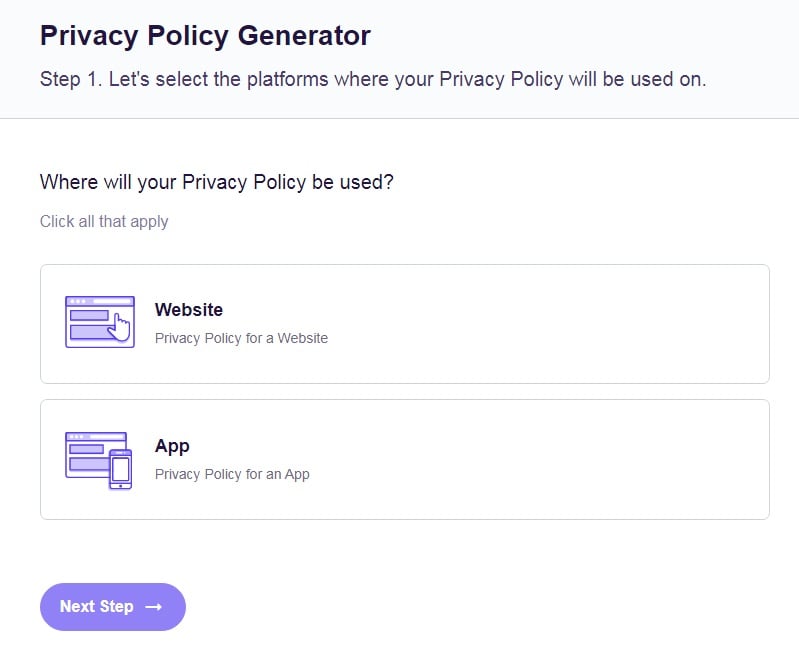
- Select where your Privacy Policy will be used:
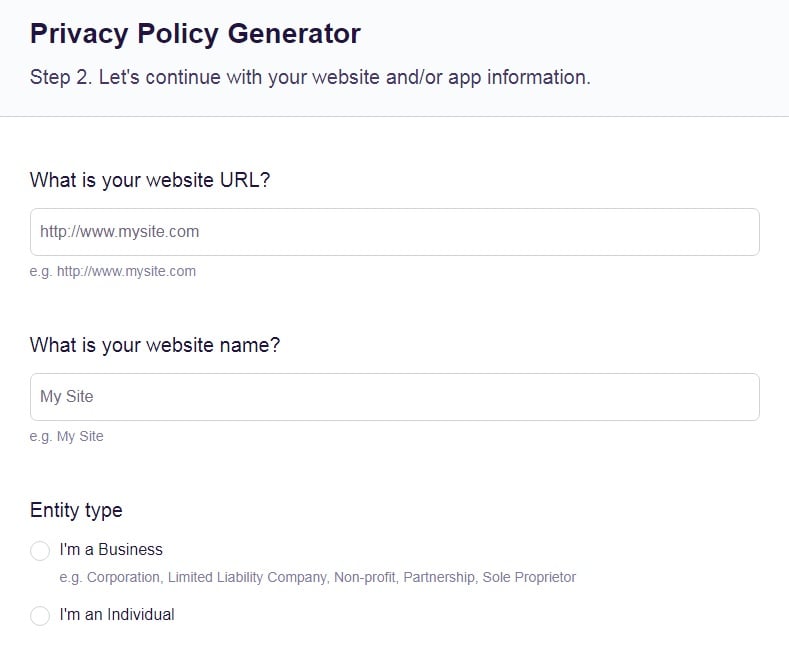
- Answer a few questions about your business:
- Enter the country and click on the "Next Step" button:
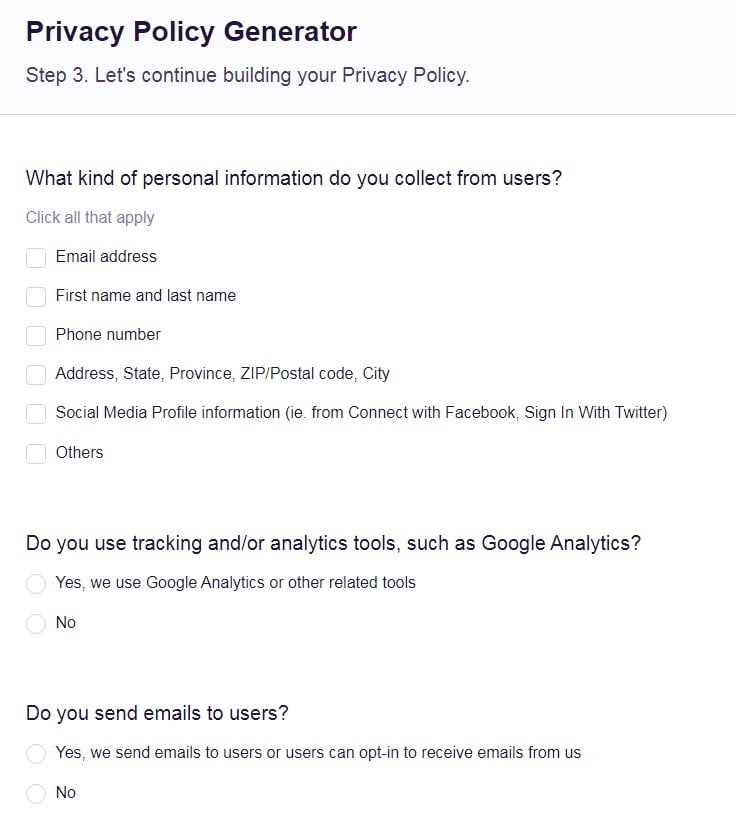
- Continue with building your Privacy Policy while answering on questions from our wizard:
-
Almost done. Now enter your email address where you'd like your new Privacy Policy sent and click on the "Generate" button and you're done.
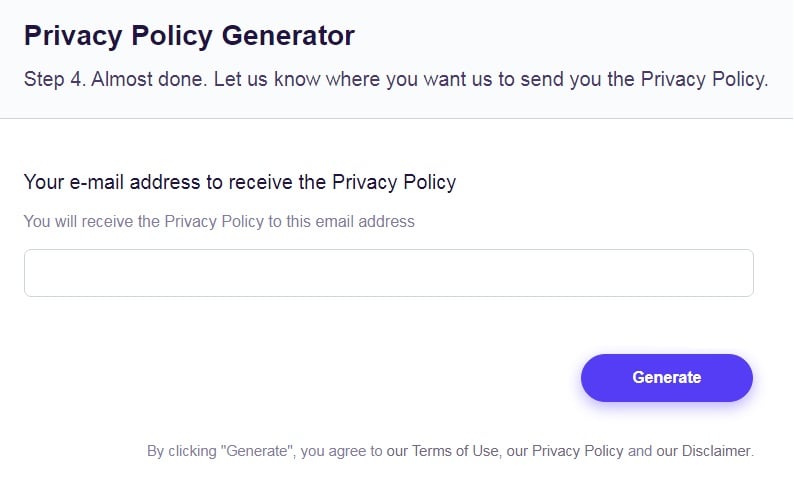
That's it. Now you can copy and paste your Privacy Policy code into your website, or link to your hosted Privacy Policy.

This article will take a detailed look at these data security safeguards to determine what they are and what practical ways can your company implement these safeguards.
What Does SHIELD Say About Reasonable Safeguards?
SHIELD contains a section about reasonable security requirements which states that:
'Any person or business that owns or licenses computerized data which includes private information of a resident of New York shall develop, implement and maintain reasonable safeguards to protect the security, confidentiality and integrity of the private information including, but not limited to, disposal of data.'
If your business owns or licenses the private information of any New York resident it must implement a data security program which includes reasonable administrative safeguards, reasonable technical safeguards and reasonable physical safeguards in order to be compliant with the act.
SHIELD gives examples of what constitutes as reasonable safeguards for each category. However, it does not give any advice about meeting each of the safeguards.
Let's look at some of the examples SHIELD gives for each safeguarding category and consider practical ways of implementing each safeguard.
It's important to note that there is no right or wrong way of implementing each safeguard as they are open to interpretation. You should consider what is reasonable and practical for your business to implement.
Reasonable Administrative Safeguards

According to SHIELD, reasonable administrative safeguards include where a business:
- Designates one or more employees to coordinate the security program
The Act suggests assigning staff to coordinate your security program. To do this you need to ensure you select suitable employees with the requisite skills and knowledge to act as coordinators.
- Identifies reasonably foreseeable internal and external risks
A practical way to identify internal and external risks is to conduct a cyber security risk assessment.
The assessment should review all of your company's policies and procedures and consider any special circumstances. You need to consider any vulnerabilities in your system and identify security gaps.
External risks refers more so to outside attacks, whereas internal risks require you to consider the possibility of your staff being coerced into breaching data security or the possibility of disgruntled ex-employees releasing sensitive data.
- Assesses the sufficiency of safeguards in place to control the identified risks
In order to assess your safeguards, you need to think about what methods of mitigation can be implemented to defend against the risks identified.
For example, you could regularly vet the security of your staff - particularly those with access to sensitive information.
You could also ensure that supervisors monitor employee's behavior and report any suspicious activity, such as a change in a member of staff's work pattern or a sudden interest in where private information is stored.
- Trains and manages employees in the security program practices and procedures
To implement this safeguard, you need to ensure your business has a robust staff training program with regard to new employees and seasoned staff alike.
To do this you could incorporate regular mandatory training and regularly remind staff of the importance of basic security measures, such as locking their screen when not in use and knowing who to report suspicious activity to.
Overall, you need to foster a culture of security and ensure staff know what's expected of them.
- Selects service providers capable of maintaining appropriate safeguards, and requires those safeguards by contract
The SHIELD Act suggests that one reasonable administrative safeguard is to only share personal information with companies who have adequate safeguards of their own. When making your selections you could aim to ensure that service providers are industry regulated or ISO-accredited.
In addition, you could create a contract for service providers to sign which requires them to undergo certain security protocols, such as undertaking regular penetration tests.
- Adjusts the security program in light of business changes or new circumstances
To do this, you should regularly review your security program and ensure you update your program accordingly when any new regulations are brought in.
Reasonable Technical Safeguards

According to the SHIELD Act, reasonable technical safeguards includes when a business:
- Assesses risks in network and software design
To properly assess risks in your network and software design, it's a good idea to hire independent contractors who can check for exploits. If this isn't possible, you can assess the risks yourself by ensuring your network and software design complies with industry standards and best practice guidelines.
- Assesses risks in information processing, transmission and storage
You would need to undertake a risk assessment to implement this safeguard. The assessment should consider how you process, transmit and store personal information and identify any weak points.
Practical things to consider when assessing storage risks include whether the data you store is encrypted and password protected. It is also a good idea to have a secure backup of the data in case your storage device fails due to an attack or technical malfunction.
With regard to transmission, consider if personal data is transmitted to third parties and whether transmission could be avoided to increase security.
When it comes to the risks of data processing, you should be extra careful when assessing the risks if you process any sensitive data such as biometric data, genetic data or children's data.
- Detects, prevents and responds to attacks or system failures
One practical way of detecting and preventing attacks is to use anti-malware software. This will allow you to monitor and protect all of your servers and devices.
Your company could also make use of hardware to search for suspicious traffic, for example, installing a firewall can help prevent denial of service attacks. Keeping your software up to date will also assist with preventing attacks.
In addition, you should implement a clear procedure which your company must follow if an attack or system failure is identified. Part of your response plan could include your system being temporarily shut down or taken offline while security is reviewed and problems are rectified.
- Regularly tests and monitors the effectiveness of key controls, systems and procedures
It is advisable to carry out regular penetration tests to uncover any vulnerabilities in your systems.
Penetration tests are used to simulate an actual cyber attack and to put you in the mindset of the cyber criminal. Doing this helps to see what weak spots you have and discover how an attacker may gain unauthorized access to your system. Once weaknesses have been identified, you can remedy them.
To perform these tests you should ensure you have staff who have appropriate technical skills and make sure they keep a record of their tests. Alternatively, you could use an accredited third party to execute the penetration tests.
Reasonable Physical Safeguards

According to SHIELD, reasonable physical safeguards includes when a business:
- Assesses the risks of information storage and disposal
To implement this safeguard you could create a risk assessment which considers the physical security of all computers within your network, even if they do not directly hold any personal data. It's important to secure all machines since an infection in one computer could potentially be used to attack further devices within the system.
You could ensure devices are physically secure by keeping them in locked cabinets when not in use and by training staff to lock their computers whenever they leave their desks.
You should also consider who has access to the place the devices are stored and ensure that only authorized personnel have the keys or password to safes.
Some companies have a secure server room which only permits access to certain staff who have been through security clearance.
- Detects, prevents and responds to intrusions
A practical way of detecting, preventing and responding to intrusions is to employ an onsite security team. CCTV cameras and security alarms can also be utilized to help detect and prevent physical instructions.
A further method is to prevent unauthorized access to your company by using staff keycards. You could ensure each member of staff has their own keycard to gain access and train staff to always wear their keycards, never give their keycard to anyone else, make sure no one is tailgating them into the building and to report any one they see who does not have their keycard clearly displayed.
To be able to effectively respond to intrusions, you should also ensure that every employee knows how to report a suspected intrusion. For example, there should be people they can report to and a phone number they can ring to report any suspicious activity.
- Prevents unauthorized access to private information during or after the collection, transportation and destruction or disposal of the same
One tip to prevent unauthorized access to private information is to make sure you know who should have access to the information and to try and limit this access to as few people as possible. Basically, only grant access to people who really need it. The people who do need access should have to use access controls such as keycards and passwords to access the information.
Further ways of preventing unauthorized access include installing security cameras and hiring a security team to monitor areas where private information is stored, collected, transported and destroyed.
- Disposes of private information within a reasonable amount of time after it is no longer needed for business purposes by erasing electronic media so that the information cannot be read or reconstructed
It's essential to ensure that your staff know how to properly dispose of private information. Your staff should be trained in the importance of proper disposal and must understand that unless electronic media is properly erased, it will be able to be reconstructed.
For example, it is not enough to simply move a document on your computer into the trash bin or to hit the delete button since the information remains stored on the hard drive. The information has merely been flagged as deleted, however it is easy to recover this data.
To securely delete data, staff must use software which writes over the top of the data storage blocks with blank data. This will ensure that there is nothing that could be recovered. This can be done both manually and automatically and you should consider the best way of doing this for your company.
Staff should also know when to permanently erase electronic media. Once again, this requires sufficient staff training on the subject.
Summary
The New York SHIELD Act aims to prevent cyber criminals from gaining access to the private information of New York residents by placing security requirements on businesses who hold their data electronically.
To comply with the act your business must have a data security program which utilizes reasonable safeguards to keep computerized data safe.
These safeguards include:
- Administrative safeguards
- Technical safeguards
- Physical safeguards
The SHIELD Act does not say exactly what is required to meet the standards of the safeguards. However, the act does give a few examples of what constitutes as reasonable safeguards for each category.
You should consider each safeguard carefully along with the practical advice given in this article to decide on the best way of implementing your businesses data security safeguards in line with SHIELD.


