
Every company that uses Information Technology (IT) should have an IT Security Policy.
Even very small companies need an IT Security Policy since they are just as vulnerable to cyberattacks as large companies. Having robust IT security measures coupled with a well drafted IT Security Policy will help to safeguard your organization.
We'll explain the benefits of this policy and show you how to create your own, with examples of the clauses your policy should include.
- 1. What is an IT Security Policy?
- 2. Why Should You Have an IT Security Policy?
- 3. What to Include in Your IT Security Policy
- 3.1. Policy Objectives
- 3.2. Scope of the Policy
- 3.3. Policy Maintenance
- 3.4. Policy Enforcement
- 3.5. User Responsibilities
- 3.6. Security Weaknesses and Vulnerabilities
- 3.7. Password Requirements
- 3.8. Proper Use of Email
- 3.9. Acceptable Use of the Internet/Social Media
- 3.10. Data Encryption
- 3.11. Anti-Virus Software
- 3.12. General Software
- 3.13. Physical/Hardware Security
- 3.14. Responding to Security Breaches
- 3.15. Non-Compliance
- 4. Summary
Use FreePrivacyPolicy.com to generate the necessary legal agreements for your website/app:
- Free Privacy Policy Generator
- Free Terms and Conditions Generator
- Free Cookies Policy Generator
- Free Disclaimer Generator
- Free EULA Generator
- Free Return & Refund Policy Generator
You check our Free Cookie Consent to start making your business legally compliant with the Cookies Directive in the EU.
What is an IT Security Policy?
An IT Security Policy, also known as a Cyber Security Policy or Information Security Policy, sets out the rules and procedures that anyone using a company's IT system must follow.
The policy will usually include guidance regarding confidentiality, system vulnerabilities, security threats, security strategies and appropriate use of IT systems. It will also make it clear who is responsible for various security measures and explain what should happen if there is a security breach.
In addition, an IT Security Policy should advise of the potential consequences if employees fail to adhere to the policy.
It's essential to keep IT Security Policies up to date as it is a living document which should be adapted to suit changing business practices.
Why Should You Have an IT Security Policy?

Regardless of size, all businesses that use IT should have an IT Security Policy to help protect the organization's assets. Here are a few additional benefits to having one:
- Litigation Protection - An IT Security Policy can help to shield your company from legal issues. The policy creates a systematic approach for your employees to follow to ensure they comply with all relevant laws, as well as with company policy.
- Prevention of Cyber Attacks - Companies without an IT Security Policy may be more vulnerable to cyberattacks since employees do not know how to effectively manage the security of IT systems to prevent breaches. The policy will make it clear who is responsible for carrying out various security duties and implementing security protocols.
- Employee Education - The IT Security Policy will tell your employees what they should be doing and what they should not be doing. Crucially, the policy will also inform people of the consequences of failing to comply. Educating your employees about IT security threats and incidents will also help to prevent accidental security breaches as staff will have a better understanding of potential security threats.
- Third Party Relations - Potential business partners may feel happier working with a company that has a robust IT Security Policy in place, particularly if any third party data is being processed.
What to Include in Your IT Security Policy

Although there is no 'one size fits all' here, there are several clauses that should be included in your IT Security Policy. Keep in mind that every clause should be drafted to suit your business security goals and practices.
Policy Objectives
This clause explains the goals of your policy and why cyber security is important.
The University of Edinburgh explains the objectives of the University's Information Security Policy at the beginning of the policy.
The policy's objectives include protecting IT assets, fostering a culture of security awareness, identifying and remedying security incidents and reassuring third parties that there is a robust IT security protocol in place. (Note this is just an excerpt):

Scope of the Policy
This clause advises readers who the policy applies to and what the policy covers in brief.
Cardiff University advises that its IT Security Policy applies to all staff, students and anyone else who accesses information, applications, systems or equipment:

Policy Maintenance
It's a good idea to inform readers who is responsible for keeping the policy up to date. This ensures that everyone understands their role with regard to policy maintenance.
The University of Bristol advises that the production and maintenance of the policy is the responsibility of the University's Chief Information Officer, but also lists the other boards and groups that play roles in the process. Members of staff are told they can suggest changes and additions through the appropriate methods:
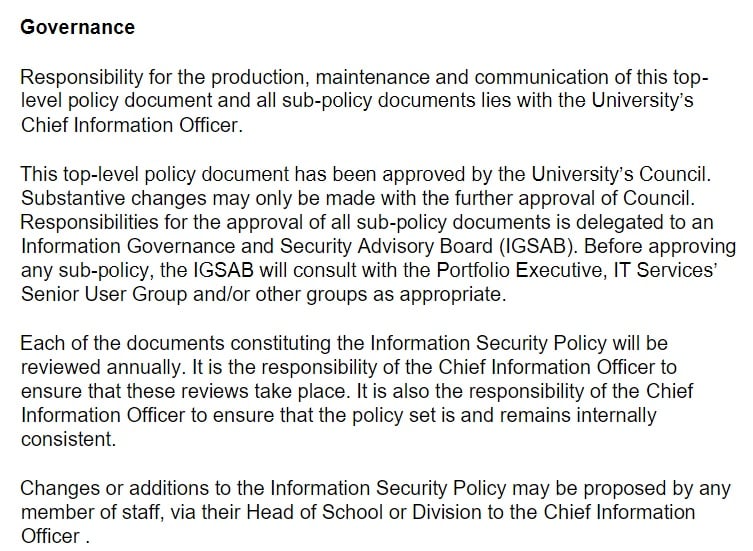
Policy Enforcement
As well as advising who is responsible for maintaining your organization's IT Security Policy, you may also wish to inform readers who is responsible for enforcing the policy.
Technology company IBM provides an overview of its IT Security Policy on the organization's website. IBM advises that the enforcement of the policy is the responsibility of the Resource Manager and also explains the role of the Security Access Manager:

User Responsibilities
This is a crucial clause which enables your business to clearly define the duties and responsibilities of users. Make sure that all users understand who is responsible for data protection and security and what they can do to ensure that your IT systems are secure.
The University of Edinburgh's IT Security Policy breaks down the role of various employees, including the Senior Management team and the Data Steward. There is also a section which advises that all users have a responsibility to comply with the policy and to report any suspected breaches. Students and alumni are also addressed:
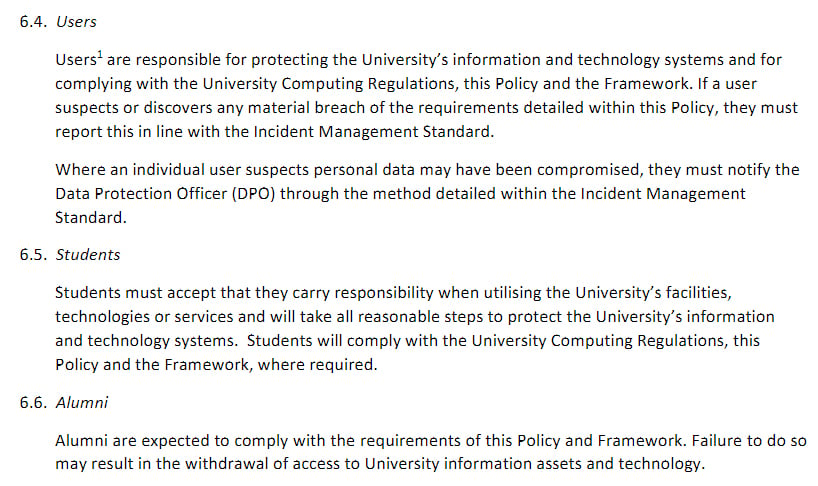
Security Weaknesses and Vulnerabilities
This clause should delve into any vulnerabilities within your IT systems and consider potential weaknesses which could be exploited by cyber criminals. After identifying these weaknesses, your IT Security Policy should explain how your organization intends to mitigate the risks.
Recruitment agency iCIMS includes a section on vulnerability management in which the company identifies vulnerabilities and ways of managing them:
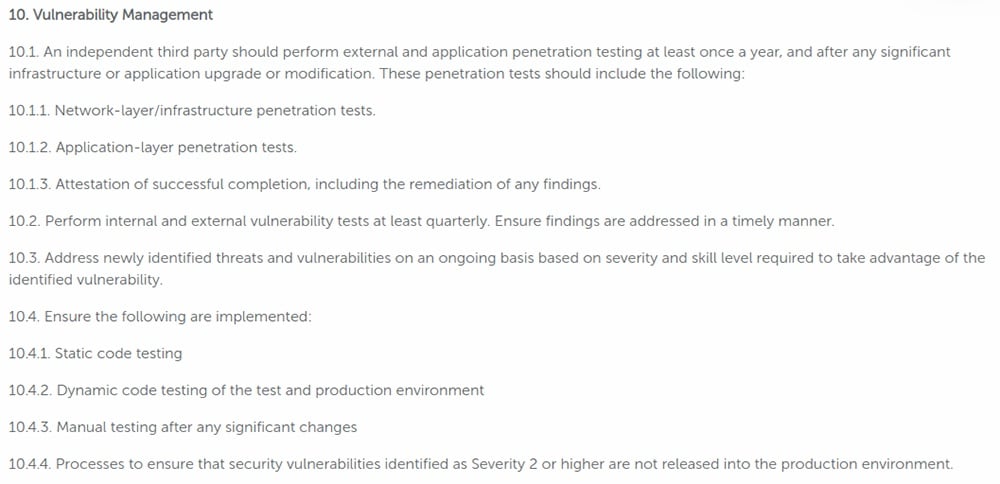
Password Requirements
It's a good idea to include a section regarding passwords in your IT Security Policy. You should advise your employees about appropriate passwords. For example, what length the password should be and how many special characters it should contain.
You should also inform users of the importance of having different passwords for different logins and advise how often passwords must be changed and if there is a prompt to update.
Other key elements include how to store passwords and your policy on sharing passwords with other people.
For example, you can remind users not to share their password with anyone.
iCIMS includes a section on 'password policy' in the company's IT Security Policy, which includes information about making a secure password as well as informing users when accounts must be locked Here's an excerpt:
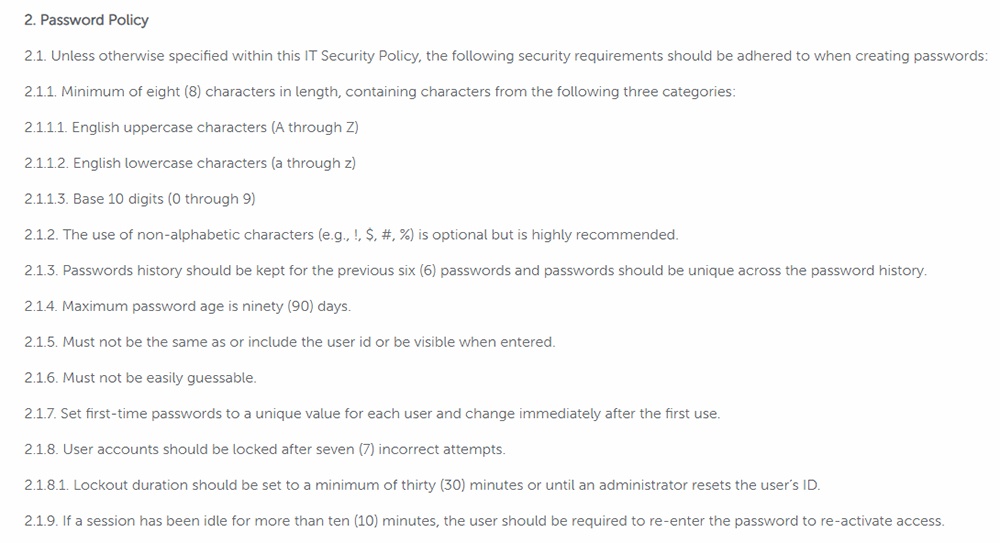
Proper Use of Email
Some companies choose to have a separate Email Use Policy, whereas others include a clause about proper email use in the IT Security Policy. There is no right or wrong way - it's whatever suits your business needs.
Either way, you should include information about your policy regarding opening email attachments.
For example, your IT Security Policy may instruct users to only open email attachments from trusted sources. This clause can also advise users of practical things such as how to block spam and scam emails and how to report suspicious emails.
You may also wish to include what information should and shouldn't be sent over email and who employees should and shouldn't share their email address with.
iCIMS includes a section on 'messaging security' in which the company advises users that all incoming email should be scanned for viruses, phishing attempts and spam:
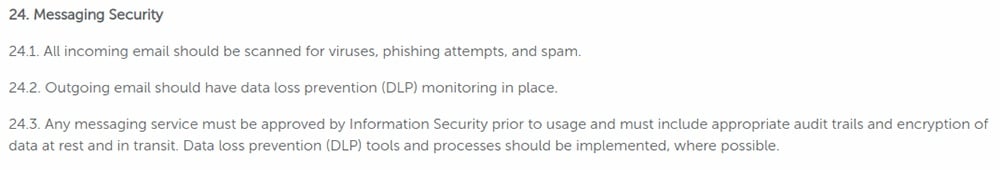
Acceptable Use of the Internet/Social Media
If you don't have a separate policy regarding social media and acceptable internet browsing, your IT Security Policy is the ideal place to include information on the use of these things.
Users should be aware of what online behavior is acceptable and what behavior is unacceptable when they are using your IT network. You should explicitly reference social media use and advise if this is acceptable and if so, if there are any limitations.
For example, some organizations ban all use of social media during work hours or on company devices, whereas others allow social media to be accessed during breaks.Some organizations also state that employees should not link their work emails to their social media pages, or should not say that they work for the company on their profile.
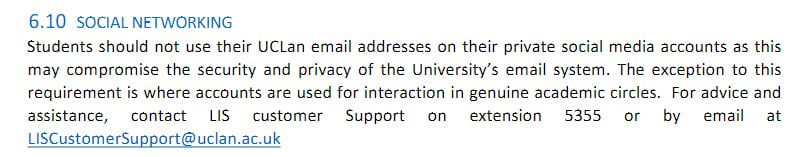
UCLan includes a brief clause on social networking which states that users should not use their UCLan email addresses on private social media accounts:
Data Encryption
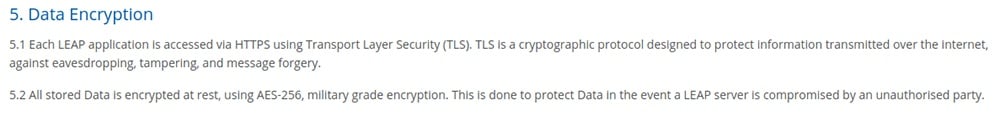
If your company uses software to encrypt certain types of data this should be explained to users.
LEAP advises how the company encrypts data in the company's Security Policy:
Anti-Virus Software
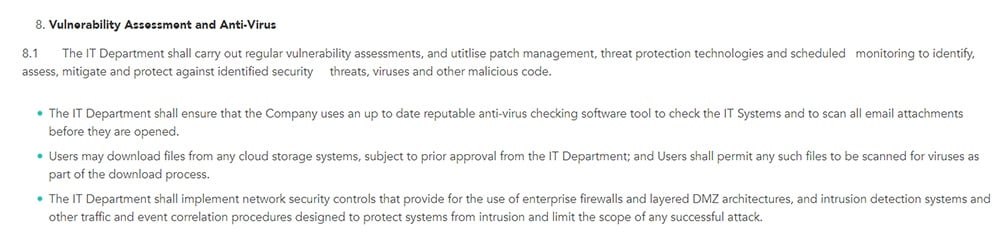
Include some information about the anti-virus software your company uses, as well as who is responsible for installing and maintaining this software.
Reddico notes that the IT Department is responsible for ensuring that the company uses an up-to-date anti-virus software tool:
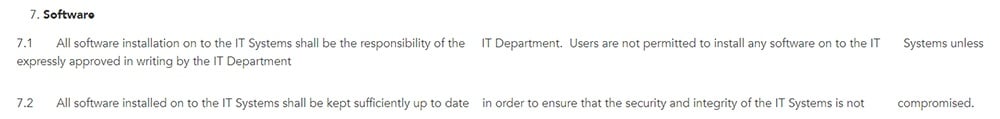
General Software
If you have limitations on what software users are allowed to install on your company-owned devices, note this in your policy. Here's how Reddico does it, with a ban unless approved in writing by the IT Department:
Physical/Hardware Security
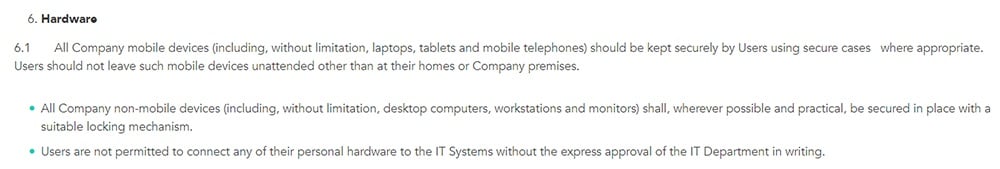
In addition to a clause about your organization's software security, you may also want to include a clause about hardware or physical security.
This should include the security of any physical files which contain sensitive or confidential information, as well the security of any devices including computers, tablets and cell phones.
You may also wish to advise employees about locking their computer screens when not in use and advise how to protect data stored on removable devices, such as USB sticks. A physical security clause is also the ideal place to mention any measures that are taken to prevent the installation of malware on removable devices.
Additionally, you can inform employees if devices should be secured at night and whether access should be allowed to other people. If your organization allows employees to work remotely or from home you should also advise of the security measures in place regarding this.
Reddico states that devices must be stored securely and should not be left unattended, along with other restrictions:
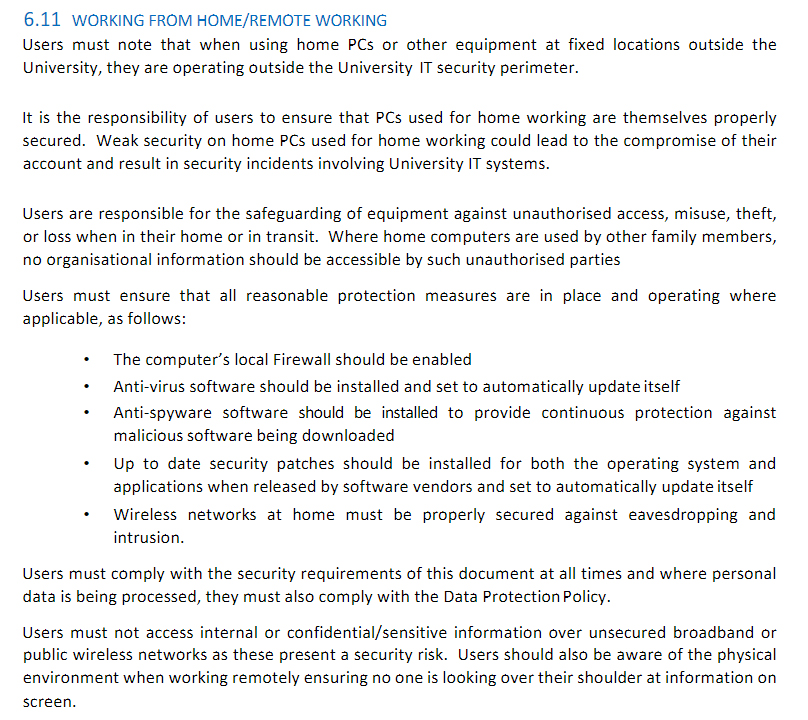
UCLan has a very robust clause directly addressing working remotely and from home. It starts by making it clear that it's the user's responsibility to stay secured when out of the University's IT security perimeter. Users are given some tips for protection measures as well as restrictions for not accessing confidential information over public wireless networks:
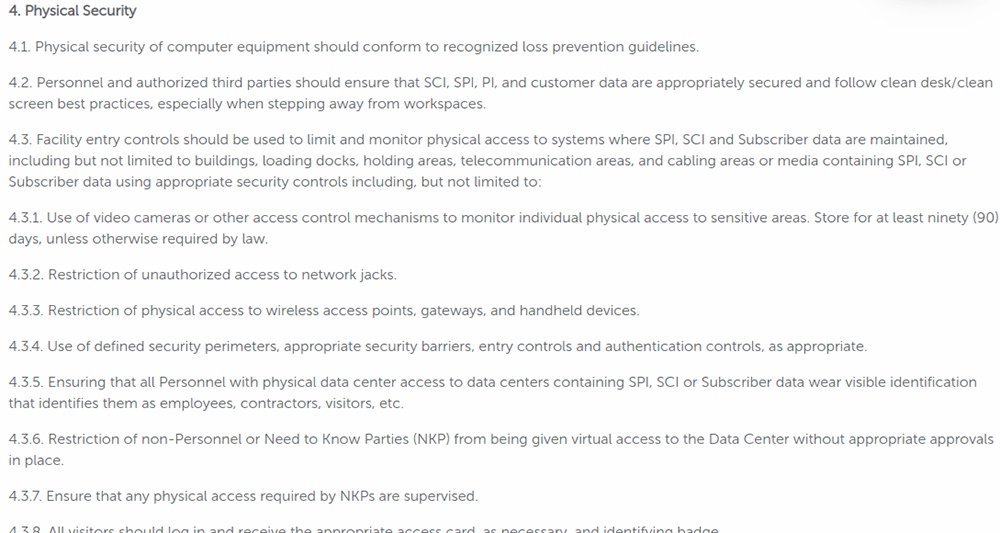
Here's how iCIMS addresses physical security and goes into detail about the company's key security measures in this area:
Responding to Security Breaches
A key clause to include is what happens in the event of a security breach. This should include information about who to inform and the various roles and duties of employees in the event of a cyberattack.
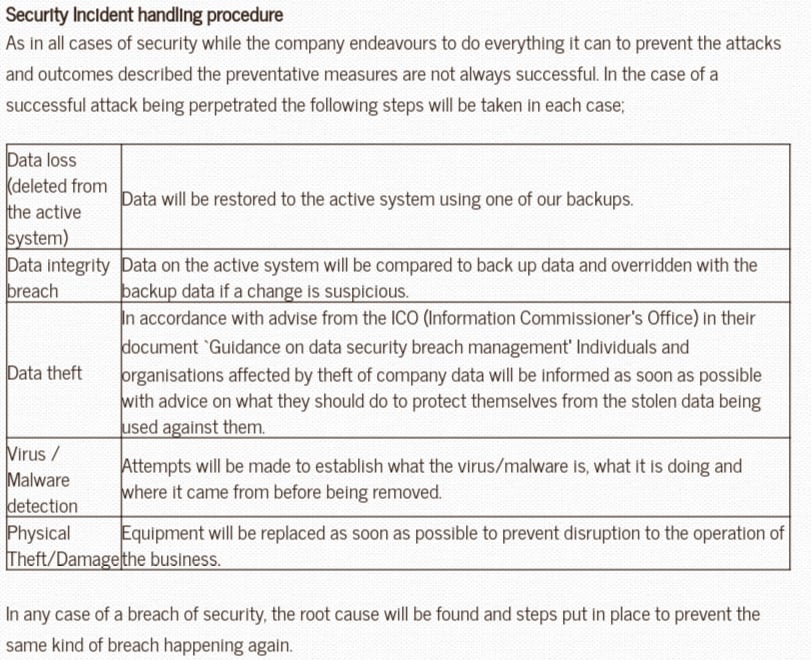
Neville Registrars includes a section that details what would happen in the event of various breaches, such as a data integrity breach or an incidence of physical theft:
Non-Compliance
Make sure your IT Security Policy includes a clause which advises users of the consequences of non-compliance with the policy.
Neville Registrars states that policy violations will lead to disciplinary action and possible legal action if the law has been violated:

Summary
If your company uses IT you should have a clear and accessible IT Security Policy, regardless of whether you have one company computer or a huge network of devices.
Having an IT Security Policy ensures that your staff is educated in the systems and measures that are in place to protect your organization from cyberattacks. Having this policy will also ensure that staff are less likely to accidentally compromise your organization's security.
In addition, an IT Security Policy makes your company less vulnerable to cyberattacks and ensures that people know how to respond to an attack or report a suspected incident.
When drafting your IT Security Policy, there are several key clauses you should consider including. Some of the most important clauses revolve around:
- User responsibilities
- Company responsibilities
- Hardware security measures
- Software security measures
- Acceptable use of company devices
- What to do in the event of a breach
As with any company policy, you should ensure that it is personalized to your business needs and that it is easily accessible to all users at any time.


