
A data breach is an incident in which data that should be confidential is accessed by somebody without authorization. This could simply mean the unauthorized person seeing the data. Alternatively it could mean the unauthorized person passing on the data or even making it publicly available.
While anyone who the data relates to is a victim of the data breach, this guide is aimed at people and organizations who control the data. We'll give you some insight into the most common data breaches and what you can do if one unfortunately occurs.
Our Free Privacy Policy Generator helps you create a custom Privacy Policy for your website and mobile app. Just follow these few simple steps and your Privacy Policy will be ready to display in minutes.
- Click on the "Free Privacy Policy Generator" button, located at the top of the website.
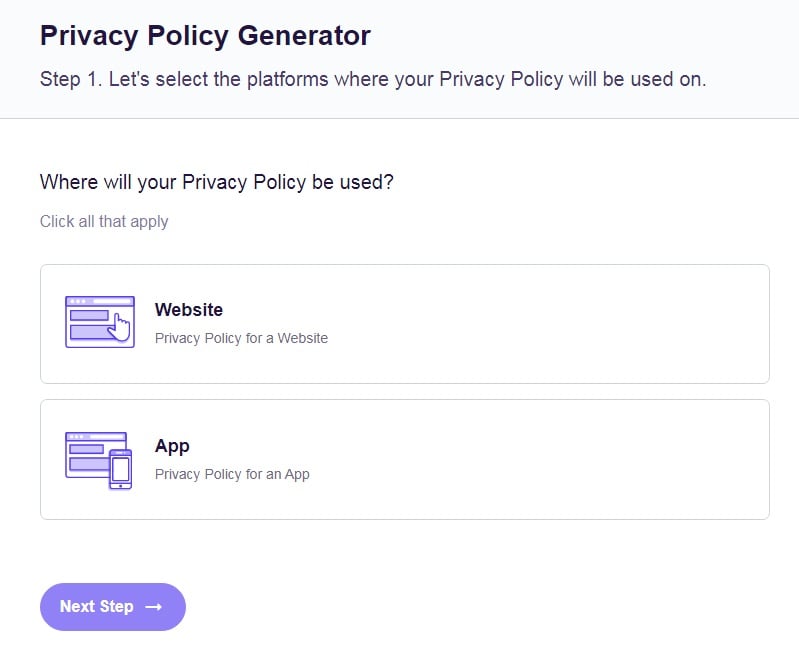
- Select where your Privacy Policy will be used:
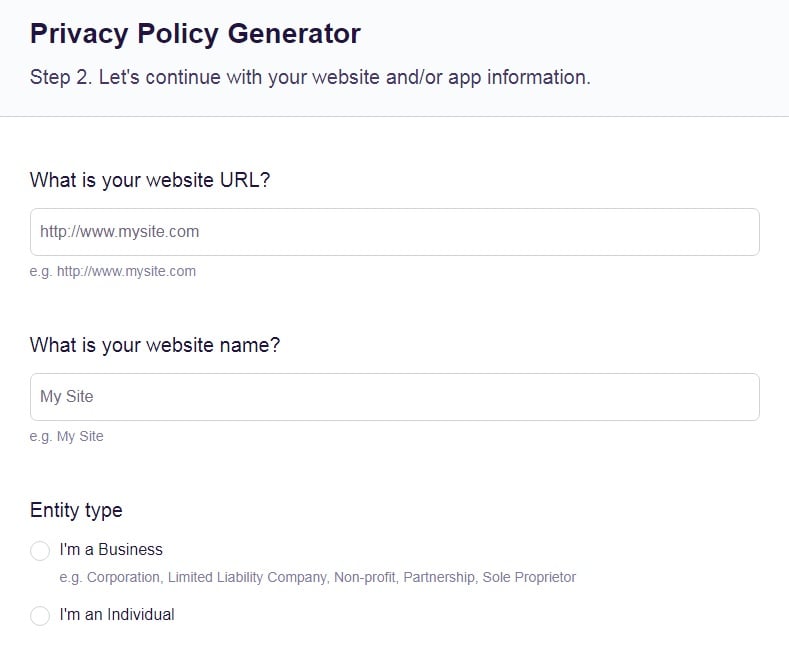
- Answer a few questions about your business:
- Enter the country and click on the "Next Step" button:
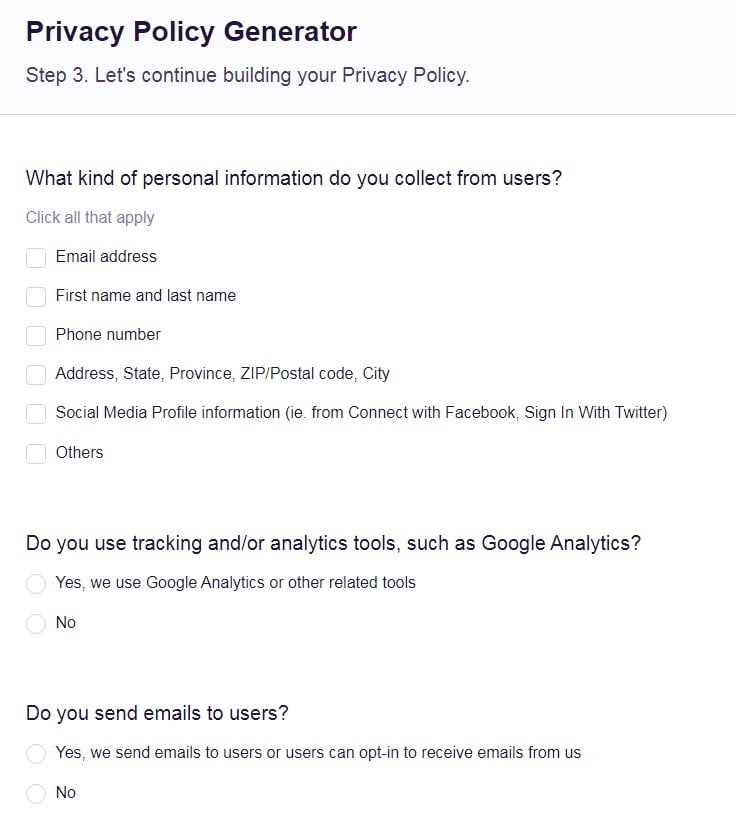
- Continue with building your Privacy Policy while answering on questions from our wizard:
-
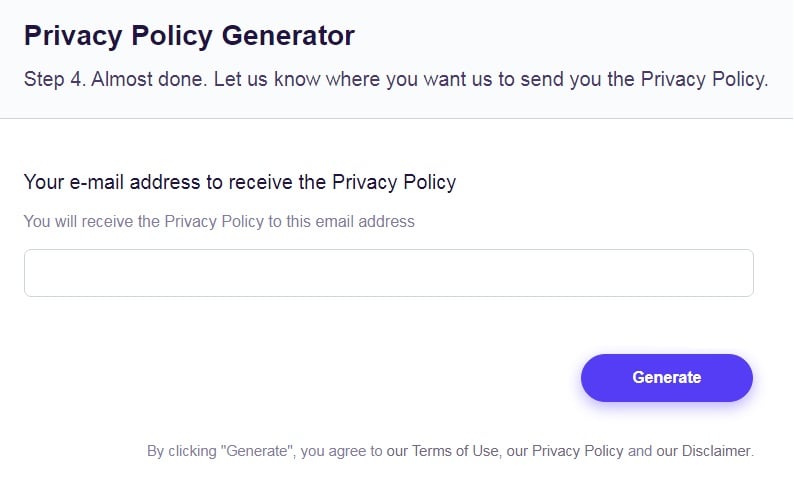
Almost done. Now enter your email address where you'd like your new Privacy Policy sent and click on the "Generate" button and you're done.
That's it. Now you can copy and paste your Privacy Policy code into your website, or link to your hosted Privacy Policy.

- 1. Types of Data Breaches
- 1.1. Brute Force
- 1.2. Targeting
- 1.3. Vulnerabilities
- 1.4. Physical Breaches
- 1.5. Inadvertent
- 2. Have a Recovery Plan
- 3. Secure and Contain the Breach
- 4. Begin an Investigation
- 5. Private Notification of Breach
- 5.1. Legal Counsel
- 5.2. Insurers
- 5.3. Financial Institutions
- 5.4. Law Enforcement
- 6. Fix and Assess the Breach
- 7. Public Notification of Breach
- 7.1. State Rules
- 7.2. Federal Rules
- 7.3. The GDPR
- 7.4. Voluntary Public Notification
- 7.5. What to Say
- 8. Review Your Security
- 9. Update Your Recovery Plan
- 10. Summary
Types of Data Breaches
Data breaches fall into several categories. We're going to cover five of them.
Brute Force
A brute force attack isn't physical but rather is a digital attack that doesn't require any knowledge of passwords or other authentication details. Instead it involves repeated attempts to log in to a system or server by trying every possible password.
Insecure passwords are particularly vulnerable to brute force, such as those which are:
- Short
- Restricted to letters rather than numbers and symbols, or
- Consist solely of words found in a dictionary
This is because the range of possible passwords is dramatically smaller in such conditions.
Targeting
A data breach could involve cybercriminals tricking a member of your staff with a bogus email or other message. In some cases the aim is to convince the recipient to open a file attachment or follow a link to a rogue web page, in both cases exposing their device and your system to malware.
In other cases the idea is to trick the person into providing login details, a technique known as phishing. Such techniques are particularly common among those who are deliberately targeting your organization for a data breach, for example for corporate espionage.
Vulnerabilities
Cybercriminals may carry out a data breach by exploiting known bugs in computer software on machines connected to the internet. Such bugs can allow people without authorization to access and sometimes alter data on your systems.
Physical Breaches
Some data breaches involve unauthorized physical access to data. This could include people breaking and entering into your property and accessing computers. It also includes theft of computers and data storage devices, both on and off your property.
Inadvertent
It's rare but possible for a data breach to occur without the involvement of a third party. For example, your organization may mistakenly upload private data to a public website. Alternatively, you could have data in a secure area of your website and mistakenly change settings such that the pages or files become publicly accessible. It's also possible that physical media such as USB drives or even paper documents could be sent to the wrong person or organization and then accessed.
Have a Recovery Plan

If your organization suffers a data breach, you need to take several steps to deal with the problem. Ideally you will have an existing recovery and response plan in place that lays out exactly what you will do. Even if you don't, you will still need to take the necessary steps.
While every situation is different, the consensus of security experts is that the following steps, usually in this order, are the key to an effective recovery plan.
- Secure and contain the breach
- Begin an investigation
- Private notification of breach
- Fix and assess the breach
- Public notification of breach
- Review your security
- Update your recovery plan
Let's explore these in more detail.
Secure and Contain the Breach

When somebody breaks into a building, the first step is to re-secure the doors and windows to prevent further breaches. It's a similar process with a data breach. You need to take immediate action to stop more data from being compromised and more damage being done.
The best ways to do this depends on the nature of the breach, but can include:
- Blocking any accounts that have been breached
- Isolating any computers or servers known to have been compromised, including physically disabling network and internet connections (Don't switch off any potentially compromised equipment as it may be needed for an investigation)
- Temporarily blocking access from the IP address where an online attack originated
- Removing information from your own website and asking search engines to remove cached or indexed copies
Begin an Investigation

The next step is to find out exactly what the breach involves. While it's important to discover how the breach happened (which can help prevent or reduce the risk of a repeat attack), it's just as important to find out exactly what happened and what data was compromised.
When you know this, you can work out the consequences of the unauthorized access. This will depend on the type of information involved and whether and how it was encrypted. You can also assess the consequences of the data being passed on from the hacker to other parties or even made public.
Such investigations are often complex technical affairs with the computer equivalent of forensic work by detectives. For this reason, many breached organizations will bring in third-party experts to carry out the investigation. As well as their experience and knowledge, they can bring fresh perspectives that your own IT staff.
Private Notification of Breach

Before going public with any breach, you need to inform several people and organizations who may need to take action immediately even if the breach itself is still a confidential manner.
Legal Counsel
A data breach can have significant legal consequences. Your own legal counsel can advise you of your obligations and any risks, including potential claims against you. They may also be able to refer you to other legal counsel who are experts on data breaches.
Insurers
A data breach will often create expenses that may be covered by either your general or specialist cybersecurity policies. Quickly reporting the breach may make claims smoother and give your insurer a chance to make any specific requests for handling the fallout.
Financial Institutions
If the breached data includes any financial information such as credit card numbers, you must tell the issuing banks as soon as possible. This can mitigate the consequences of the breach both for you and cardholders.
Law Enforcement
If the data breach was caused by anything other than your own error, it is likely to be a crime. You should contact the local police department with details of the breach. This not only lets them investigate the breach itself, but also prepare for possible crimes such as identify theft that result from the breach.
Fix and Assess the Breach

The next step is to go beyond securing your systems and now concentrate on fixing the problems to get everything back to normal working order.
You also need to fully assess the impact of the breach and how it happened. In particular you need to make sure any vulnerabilities are plugged so that the attack cannot be replicated. This will avoid encouraging other cybercriminals and hackers to attempt to repeat the attack if and when you make the details of the breach public.
Public Notification of Breach

Once you are confident the breach has been fixed, consider whether you should (or must) notify the public. This can involve state and federal rules.
State Rules
In the US, most legal requirements to go public about a breach are set down by individual states. The rules vary significantly, so you will need to check with state authorities or seek out specialized legal advice. Some questions to ask to help decide if you must report a breach are:
- What is the definition of personal data under the state rules?
- Do you have to report all breaches or is there a threshold for the potential risk of harm?
- Do you need to report to the attorney general, report to a state agency, or make a public notice?
- Is there a time limit on making a report?
- Do the rules differ depending on whether the breach involves paper or electronic documents?
- Does it matter whether the data breach involves encrypted or unencrypted data?
- What must I include in the notification?
Federal Rules
The main federal rules on reporting data breaches involves health information.
The Federal Trade Commission has rules that apply if the breach meets five criteria:
- You are a vendor of personal health records (or deal with such a vendor) and aren't covered by the Health Insurance Portability and Accountability Act (HIPAA)
- The breach involves "unauthorized acquisition" of data
- The data includes health information that identifies or could identify an individual
- The data is unsecured, meaning unencrypted
- The data is part of an electronic personal health report
In such cases you must tell:
- All affected individuals within 60 days
- The FTC within 60 days, though this deadline falls to 10 days if the data covers more than 500 people
- The media within 60 days if the data covers more than 500 people from the same state
This report form from the FTC shows the information you'll need to provide:
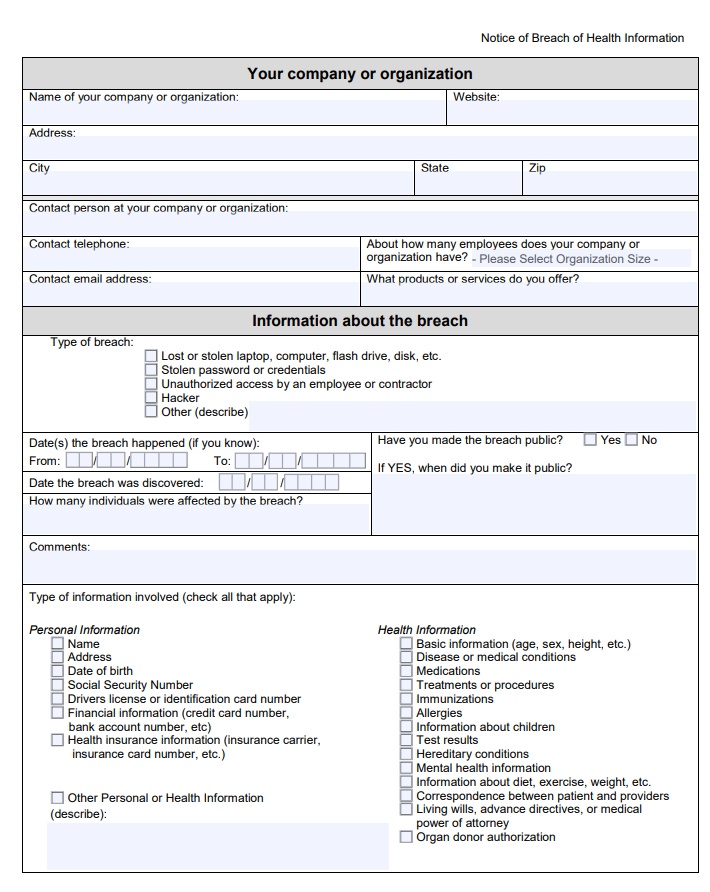
The first page is reserved for basic information such as your company's name and contact information, the date of the breach, what information is affected and how many people were affected.
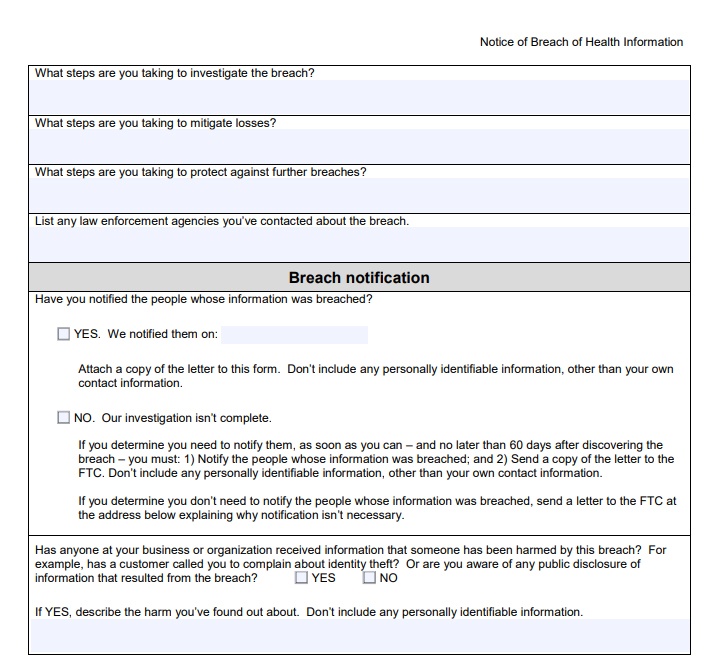
The second page is more subjective and open-ended, asking questions about what steps the company is taking when it comes to investigations, mitigations and contacting law enforcement agencies:
If you are covered by HIPAA you must notify the Secretary of the US Department of Health and Human Services through the HHS website. The deadline is 60 days if the data covers at least 500 people. If the data covers fewer than 500 people, the deadline is 60 days after the end of the calendar year in which you discover the breach.
For all FTC notifications and for HIPAA notifications where the breach covers data of at least 500 people, the rules say you should make the notification "without reasonable delay."
In practical terms this means you should make the notification as soon as you have the relevant information. You should not intentionally delay the notification just because you are still within the deadline.
If you are a publicly traded company, you must disclose "material cybersecurity incidents" in subsequent financial filings. This is because investors have the right to know about data breaches and associated risks that could affect the value of the company. The SEC has the right to fine companies that fail to do this.
The GDPR
If you fall under the scope of the GDPR and your company has a data breach that likely to result in "a high risk to the rights and freedoms of the data subjects whose data is breached," you'll need to notify data subjects of the breach within 72 hours of it occurring.
There are a few exceptions and additional requirements. You can learn more about the GDPR's data breach notice requirements in our article on the topic.
Voluntary Public Notification
You should consider making a public notification even if you aren't legally required to do so.
While going public may bring some bad publicity, it can also establish trust among customers compared with the risk of the breach coming to light later on and creating the impression you are trying to cover something up.
When deciding whether to go public, consider whether and how knowing about the breach will benefit your customers and other people whose data was involved. Notification could give people the opportunity to take actions such as changing passwords or looking out for attempted fraud, reducing potential harm.
Before going public, check with your legal counsel to see if doing so may have any legal implications. You should also check with the police or other relevant law enforcement to make sure you don't compromise any investigation. It's usually sensible to set up a point of contact within your organization to deal with responses and queries that follow the notification.
What to Say
If you're required to make a notification under state or federal regulations, you may have to follow a set template. If not, some of the key information to include is as follows:
- A clear overview of what happened and what data was involved
- A clear overview of what steps you've taken to fix the breach and deal with the consequences
- Details of what affected people need to do themselves
- Details of how affected people can contact you
- Details of how you will contact affected people with any further details. (This reduces the risk that scammers will take advantage, for example with phishing scams relating to the breach.)
This extract from a notification by Quora clearly shows what it was doing in response to the breach and what users needed to do:
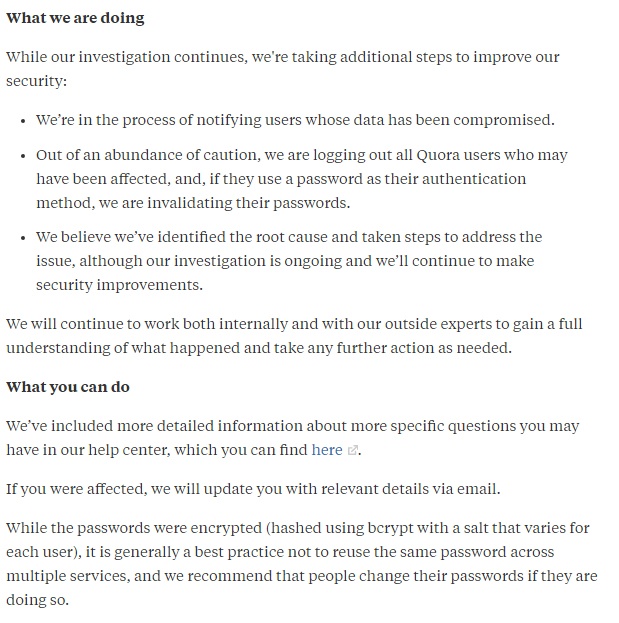
The FTC suggests you should point affected people towards the IdentityTheft.gov website. It also says you should consider offering to pay for a year's credit monitoring service for affected people.
This is an example document from the FTC to attach to your public notification and help users decide what to do next:

Including something like this with your public breach notification will be very helpful to your users and they'll appreciate the guidance, suggestions and efforts of yours during a frustrating time. The better you handle a data breach, the less likely you are to have your reputation damaged beyond repair with affected customers.
Review Your Security

Once you've taken all the previous steps, it's time for a full security audit to identify and reduce the risks of future data breaches.
Part of this audit should be procedural. For example, reviewing who has access to which files and systems and making sure passwords and other authentication measures are adequate.
Part of this audit should be technical. for example, scans of your system's public ports and servers to identify breaches, or reviews of whether internal measures such as sandboxing can reduce the impact of an external breach.
As with the investigation stage, bringing in external experts for an independent perspective and assessment may be worthwhile.
Update Your Recovery Plan

The final step after a data breach is to review your breach recovery plan, or write one if you didn't have one to start with. You will need to identify any points where your plan was not adequate or suitable.
In many cases, shortcomings in your plan can only be exposed by the reality of dealing with a breach, so this is an opportunity to learn from experience. One important point to watch for is that your plan not only covers what happens after a breach, but also who is responsible for which task.
Summary
Let's review what you need to know to deal with a data breach:
- Data breaches can involve targeted attacks, brute force, bugs and vulnerabilities, physical breaches and inadvertent exposure of data
- Having a recovery plan in place beforehand makes dealing with a breach much easier
- Securing and containing the breach is the number one priority after discovering it
- Once the breach is secured, begin an investigation, possible with the help of external experts
- The people you need to tell quickly include legal counsel, insurers, financial institutions and law enforcement
- Once the initial investigation is complete, fix and assess the breach
- Check if you need to make a public notification under state or federal rules. Consider making one voluntarily as well, giving affected people clear and actionable information.
- The final steps are to review your security and then review and update your recovery plan in light of your experience


